Hand Crafted Artisan Compiled Binary
This post describes the cmsc430 challenge by aparker, in the rev category of University of Maryland Capture The Flag 2024. The challenge provides a single binary, chal, which the author states “was compiled by an hand-crafted, artisan racket compiler”.
Die tells us it was a C/C++ program compiled by GCC. Loading the binary into Binary Ninja and jumping to the _start function, we see a typical libc entry point referencing the main function:
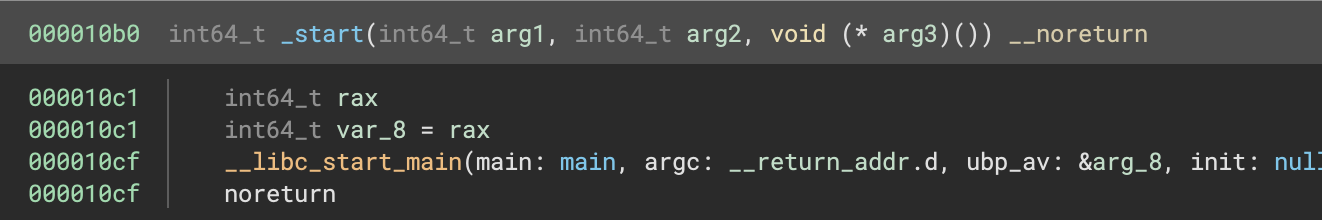
Jumping to main:
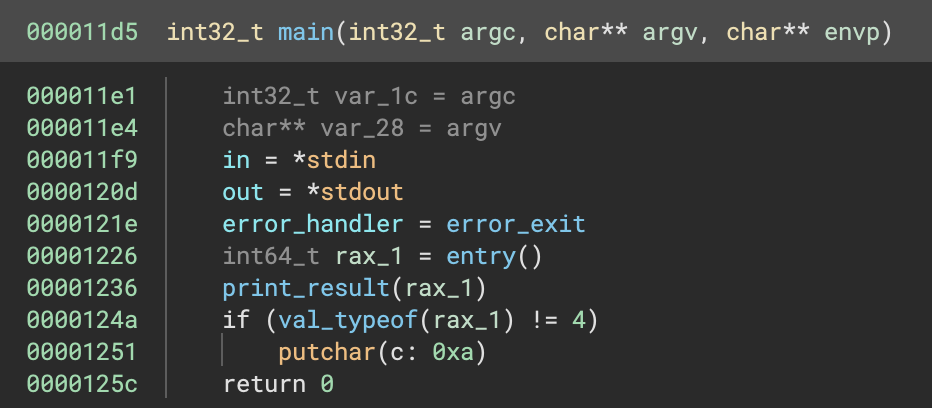
Looks like it gets access to stdin and stdout, calls entry then calls another function to print the result. The entry function looks like:
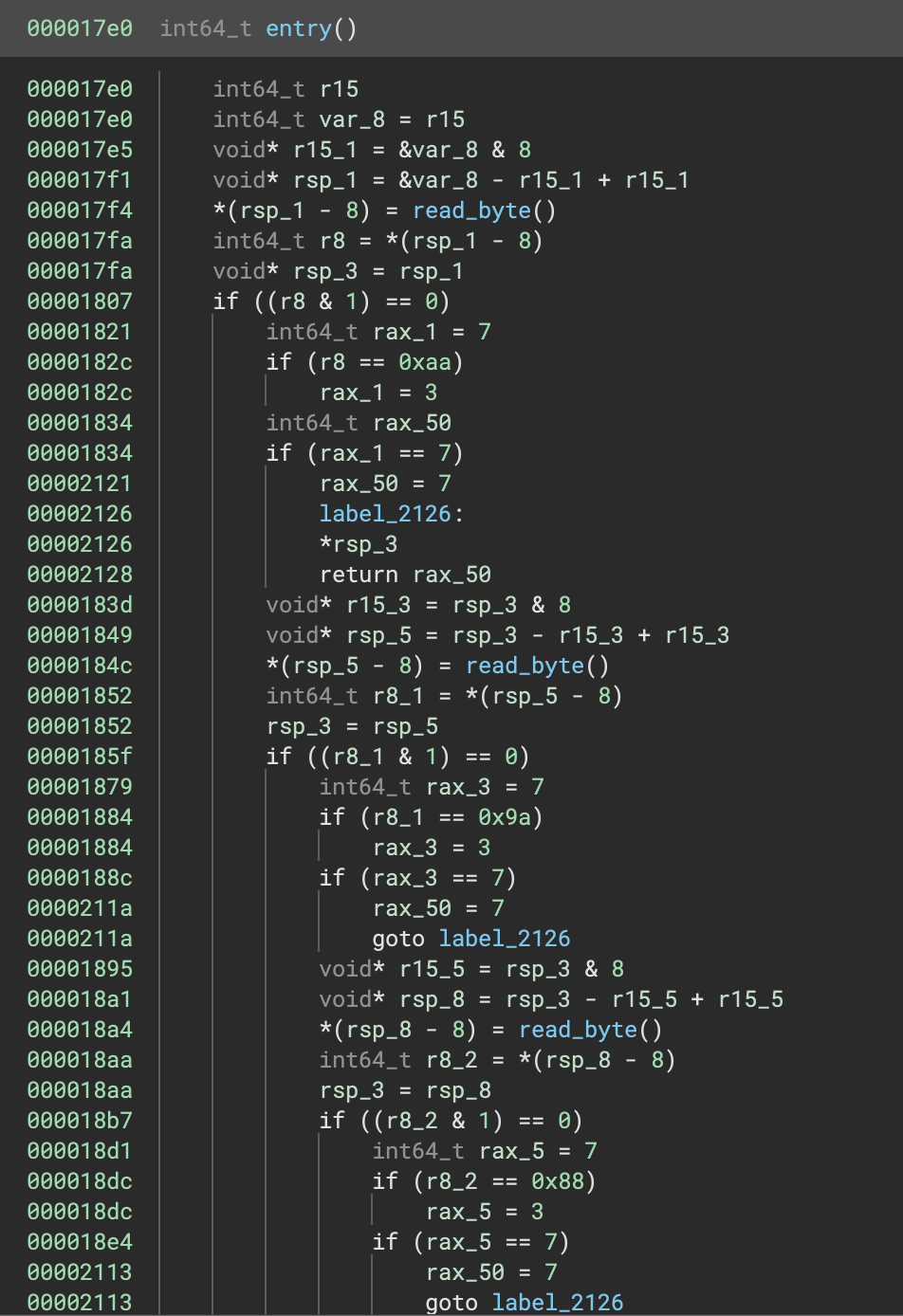
This looks like reading the flag character by character, and checking each char code against fixed values. The pattern continues on for the rest of the function. However the values it’s checking against (0xaa, 0x9a, 0x88 etc.) don’t match up to characters we’d expect to be in a flag.
To explain this we can take a look at what read_byte does:
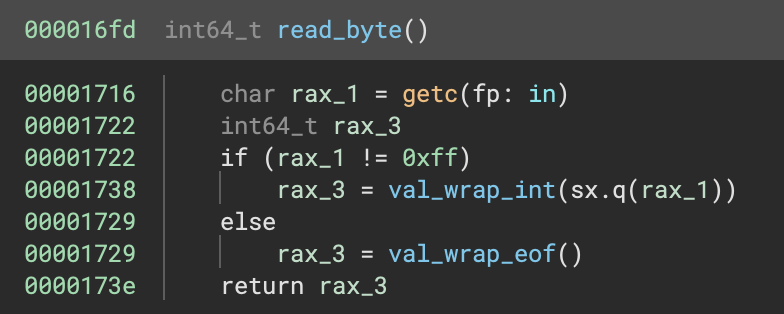
This seems as expected, but what does val_wrap_int do?
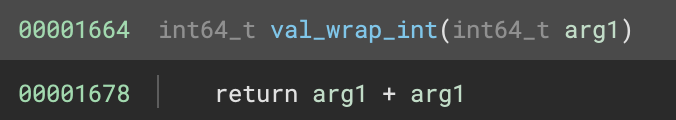
That explains it! The flag character codes are doubled before being validated, so we can divide the values we saw earlier by 2 to get the correct flag. Doing so gives us the flag
UMDCTF{shout_out_to_jose}
Epilogue
The source code for the challenge can be found here.